I use ublock origin with no global cosmetic filtering, only some specific cosmetic filtering that I added manually, nextdns with a shit ton of block lists, a hosts file with hagezi ultimate mini.
It didn’t detect anything:
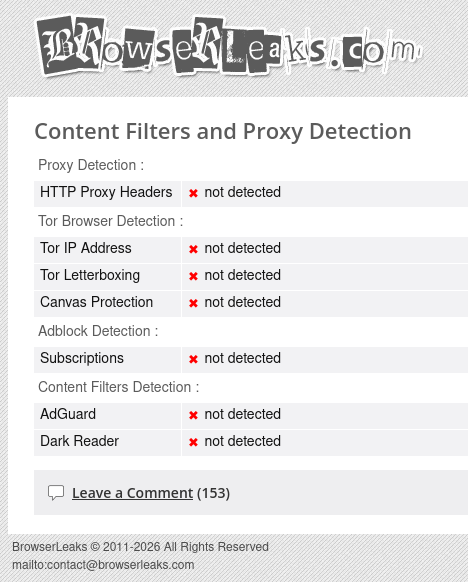
Edit: I’m using the adguard blocklist
Edit 2:
The website does only some downloads that are pattern matched only by some block lists, if you don’t use certain rules, it doesn’t get caught. It doesn’t use other domains, or any other thing, just downloads files that look like domains or parts of the URL of the pattern matched rules.
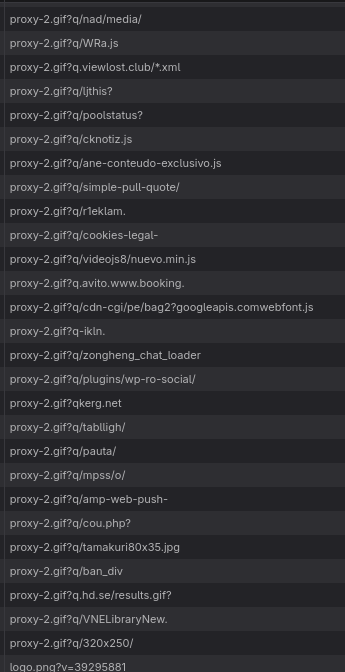
So if the filter list use domain blocking, it won’t get caught by the website. If the filter list use simple URL pattern matching to get the domain or part of the path, then it will get blocked.
I would guess it’s because you don’t download blocked resources so the server will know
Checking the network traffic, it does a series of “s_a_f_e…Overflow” (indicating safe buffer overflows?), replacing them with filter-list-specific domains after the overflow (the address after the long string of characters); triggering uBlock to block these requests?
These urls were all blocked by my hosts file, so it seems to trigger something else.
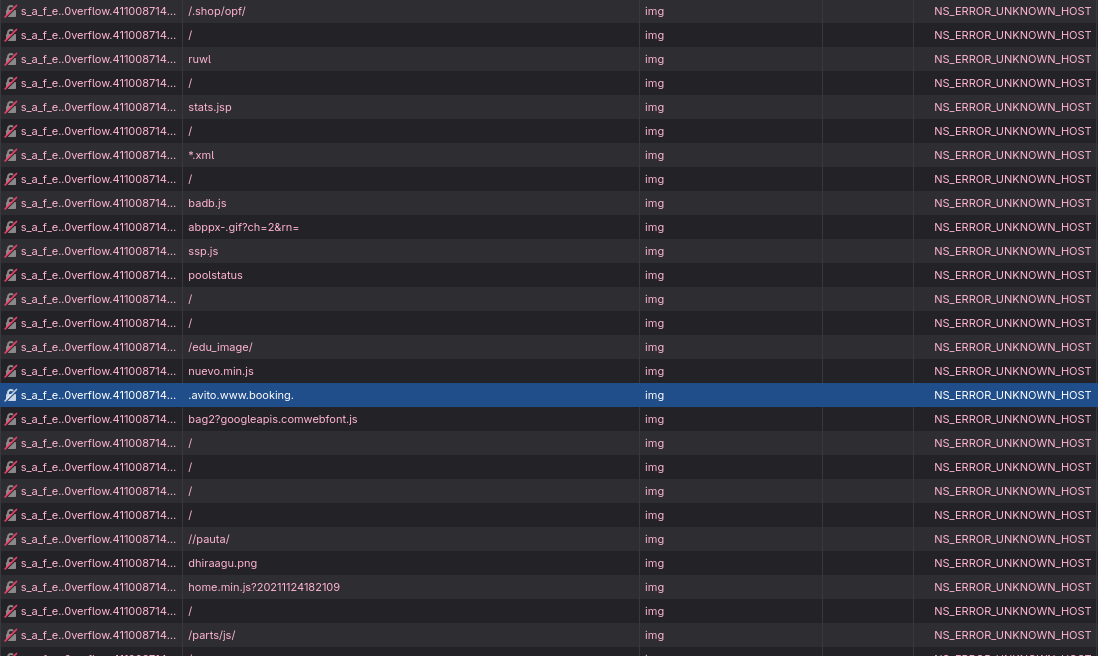
Edit: it didn’t do anything it seems, it’s all “not detected”.
Hmm, maybe it also monitors for changes to the DOM: cosmetic filtering done by uBlock (to hide/remove containers for these elements)? Something which network filtering by itself cannot do?
It looks like it’s searching for pattern matched blocked stuff, if it’s blocked on both the overflow url and the normal url, then the filter list is blocking the element. But it’s only a guess,
It’s very wrong about my entire setup, but it’ll be because it can tell you didn’t download some things




